Companies around the world face mounting pressures to defend their most important assets – whether that be physical assets or confidential organizational data. For many of these entities, the best line of defense against increasingly sophisticated security threats is a Security Operations Center (SOC). These powerful centers play a critical role in avoiding security failures that directly impact your brand, operations, and the overall growth of your company. The three key components to have a successful SOC are the people, the tools and processes, and the technology. Any operator of a SOC will tell you that, alongside all the benefits of a high-performing center, there are several challenges as well.
In this blog, we’ll explain the top three challenges that every SOC encounters and why you should prepare your operations to overcome them.
Challenge #1: The Talent Shortage and Security Skills Gap
While security threats continue to evolve, so too must an enterprise’s line of defense. A well-equipped SOC team can provide 24/7 detection, response, and monitoring of your operations and the IT infrastructure and data. SOCs often fall short when trying to find the skilled professionals necessary to run the operation center. An operation center includes teams of security analysts, incident responders, specific-threat hunters, and of course, SOC managers. The talent and specific skillset aren’t very easy to find and it’s a challenge felt worldwide.
In a recent Deloitte survey of technology industry leaders, one respondent remarked about the hardest-to-fill roles: “On the technical side, I would say security and system architects. People that understand how things fit together. I call them unicorns. Somebody that can actually sit down and think about how software and the network and hardware and cloud and data all fit together. That’s really hard to find.”
Not only does this talent shortage directly impact a SOC’s ability to stay abreast of the latest threats, but it also makes it difficult to keep your technology ahead of your competitors. The burden will end up falling on the skilled and experienced team members that you already have and can potentially lead to quick burnout, high turnover, and increased errors that can often go undetected and take extra time to fix.

Challenge #2: The Integration and Interoperability of Security Tools
SOCs leverage a diverse arsenal of security tools, like:
- Security Information and Event Management (SIEM) systems;
- Intrusion detection systems;
- Endpoint detection and response (EDR);
- User and entity behavior analytics (UEBA);
- Threat intelligence platforms.
While these tools can make a significant impact on an SOC’s ability to safeguard organizational assets, the challenge lies in ensuring that these tools can work together seamlessly.
Much like a conductor trying to synchronize an entire symphony of instruments, an SOC’s success is reliant on the harmony of its tools. In the SOC realm, issues in integration and interoperability arise when these tools fail to communicate effectively, leading to inefficiencies, security blind spots, and a fragmented view of the threat landscape. To have a successful SOC, you must focus on making sure that your unique technologies all work in sync to avoid security coverage gaps and guarantee that your workflows perform at their best.

Challenge #3: Making Sure Your SOC is Flexible and Adaptable to Current (and Future) Threats
Traditional Customer Experience Management (CEM) systems have long been a common tool found within SOCs, serving as the foundation for operations management. These tools commonly offer structured data display to ultimately drive operational cohesion. However, these tools have their shortcomings, as well. Despite their merits, traditional CEM systems exhibit limitations when faced with the demands of Security Operation Centers (SOCs) that need to constantly evolve and deal with new threats and concerns. What might have worked for you in the past, might not be what sets you up for success in the future. That rigidity becomes a stumbling block, making it challenging to seamlessly integrate and display new tools and technologies, as well as adapt quickly to any new complications.
Solutions Created with These Challenges in Mind
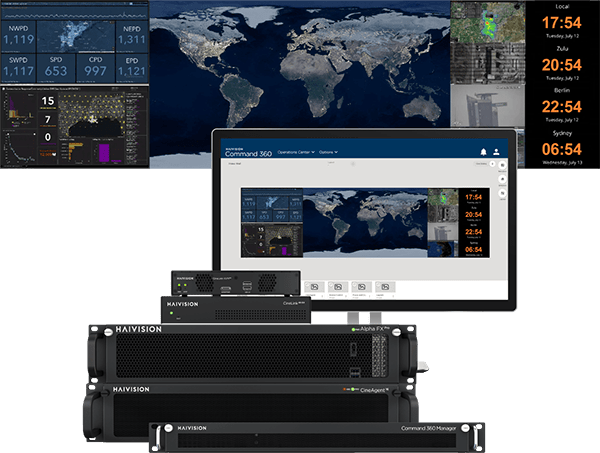
Imagine a command center equipped with the ability to swiftly integrate and display new tools. We’ve got you covered! Haivision Command 360 exemplifies the flexibility and adaptability that SOCs require, addressing the important operational challenges above. Its seamless approach ensures that SOCs can effortlessly incorporate new technologies, strengthening their defenses against the mounting threat landscape. It allows you to not just ‘get with the times’ but be fully adaptable and future-proof your operations by having flexible and agnostic content display abilities. What this means is that independent of the content you’d like to display, Command 360 will allow you to manage and control ANY content. The agnostic approach means it can work with most content technology and applications found today on the market. It also boasts ease-of-use technology that allows for even non- or low-technical people to operate, which can help with the skill shortage being experienced globally.
Navigating the realm of cybersecurity demands a clear understanding and proactive handling of the challenges faced by those establishing or considering a SOC. Challenges are not insurmountable obstacles; instead, they serve as opportunities for growth and enhancement in security protocols. Because the Haivision team is aware of these challenges, we’ve also been able to prepare for them.